Veeam has recently released version 12.1, introducing various new features. In my laboratory environment, I tested the Malware Detection functionality and would like to provide some insights here, as well as discuss a few of the new features included in this latest version. This article is based solely on my personal experiences in the lab.
Inline Malware Detection:
This involves an inline analysis of data, utilizing machine learning to identify encrypted data that was previously unencrypted. Attention is also given to indicators such as the presence of Onion links.
The load is transferred to the Backup Proxy, hence it is essential that it has adequate resources and is not already operating at full capacity. No additional configuration is necessary, as Veeam automatically provides and integrates this function with the update.
Analysis of fileserver activities:
In the context of GFSI (Guest File System Indexing) for file servers, the guest file system is scanned for known malware file extensions and evaluated, using multiple indicators for examination. For instance, the renaming or bulk deletion of existing files is monitored and reported, allowing for subsequent review. Particularly, unknown and/or unusual file extensions are noted and can be specifically scrutinized and validated.
This feature is independent of the aforementioned inline analysis and requires active GFSI. Since the definitions for this function are updated at regular intervals from Veeam servers, an internet connection to Veeam is necessary. A manual update option is available, but it involves additional administrative effort.
Early Threat Detection:
Veeam provides an interface through the Veeam Incident API, which can be utilized by NDR/MDR/XDR tools. This enables the early detection of any infection of the backup server or backups. In the event of an infection, all backup files from the time of the infection are marked as infected. Concurrently, Veeam can be instructed to perform a separate backup of a specific workload, prior to widespread damage being caused by malware.
YARA scan:
YARA, a pattern recognition framework developed by VirusTotal for the detection and research of malware, is also used in antivirus software.
Within Veeam, YARA assists in analyzing existing backup files and pinpointing the time when malware infiltrated the production system and consequently the backups. These scans are based on the SureBackup method and can be scheduled or automated.
Important: This feature requires the Veeam Data Platform Advanced or Premium edition!
Event forwarding:
Veeam is capable of forwarding a threat, regardless of its type, to a SIEM (Security Information and Event Management) system, thereby ensuring transparency. Additionally, the Syslog function has been enhanced, allowing for much quicker and more efficient responses to threats and attacks.
Labor-Szenario:
In my lab environment, I have installed a Veeam infrastructure that includes the following components:
KH-VMGR-01: Virtual Backup Server (VBR Server)
KH-VEM-01: Virtual Enterprise Manager Server
KH-VONE-01: Virtual Veeam ONE Server
KH-VPR-01: Virtual Proxy Server with RDM as backup target (based on ESXi)
KH-BETA-01: Test VM that can be used for loading viruses, etc.
The VM KH-BETA-01 was backed up multiple times to familiarize it within Veeam and to create several “clean” restore points. Subsequently, I copied an EICAR test file onto the system (path: Downloads) and then created backups again. The Windows Defender triggered multiple alerts during the file download, so I declared the Downloads folder as an exclusion in the Defender for this scenario.
Such actions should not be conducted in a production environment!
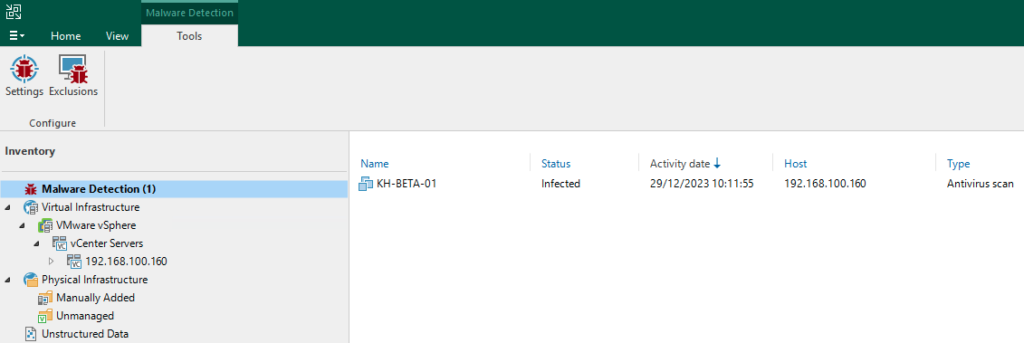
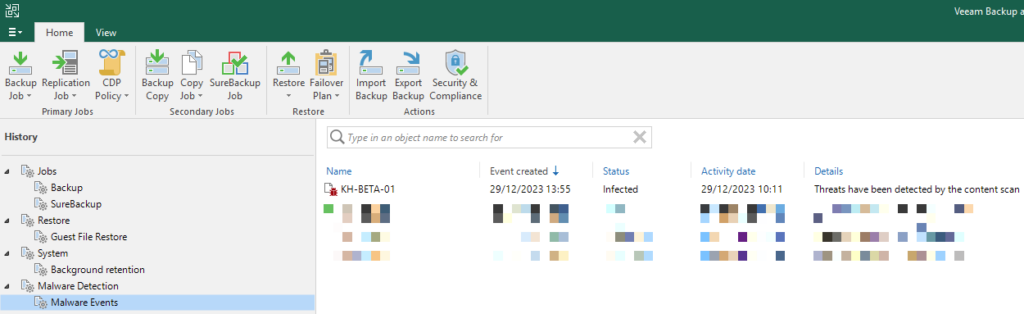
The Malware Detection immediately triggers in this case. The infection is also displayed within the overview in the Veeam console:
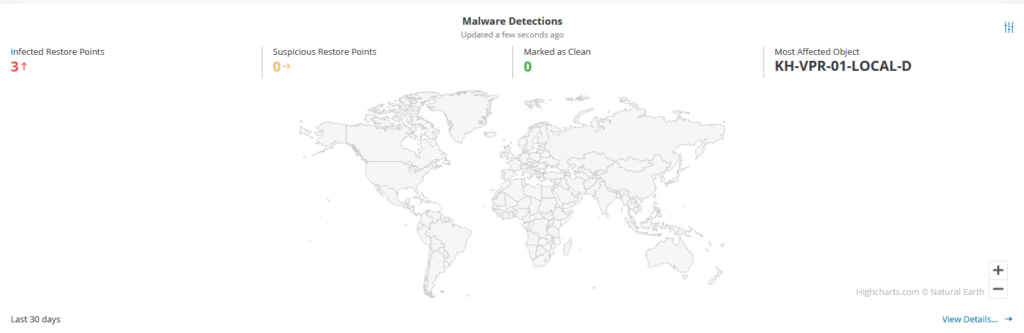
Important: Veeam ONE is necessary for the full functionality of analytics, as mentioned above!
Within Veeam ONE, you will then receive a corresponding alarm directly:
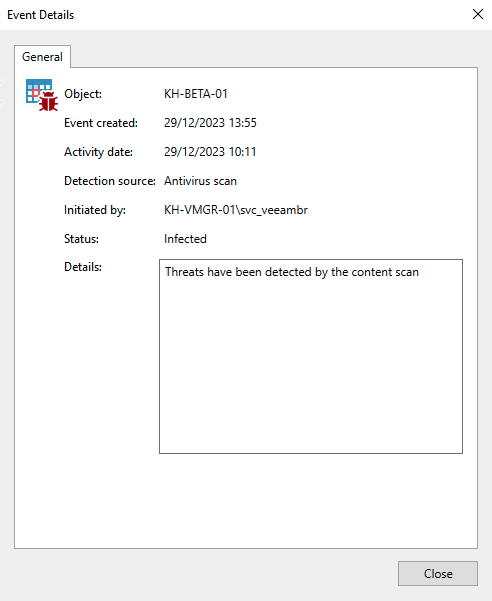
With Veeam ONE, the following report can be generated, which provides more detailed information:
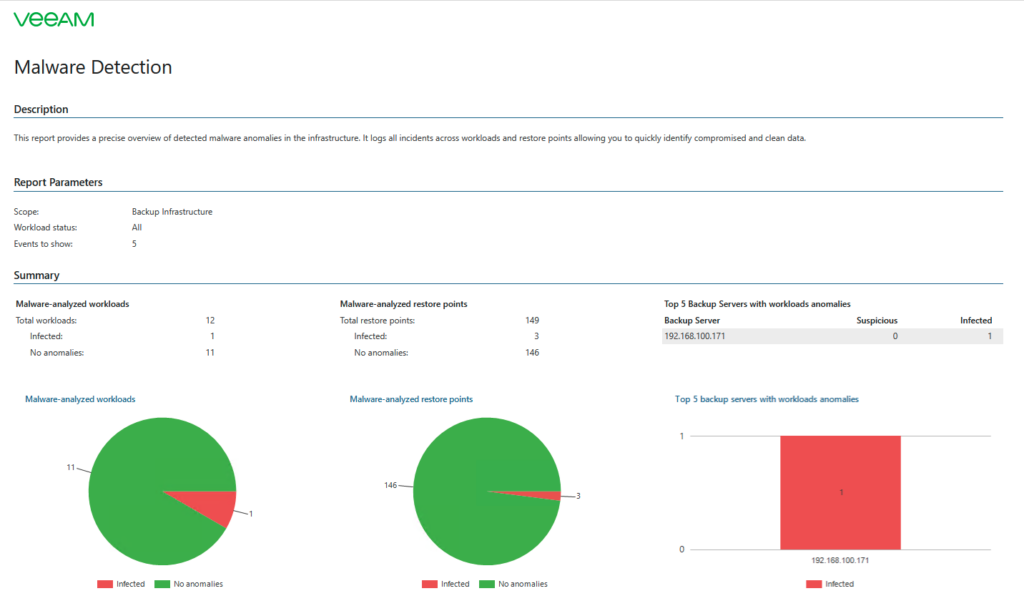
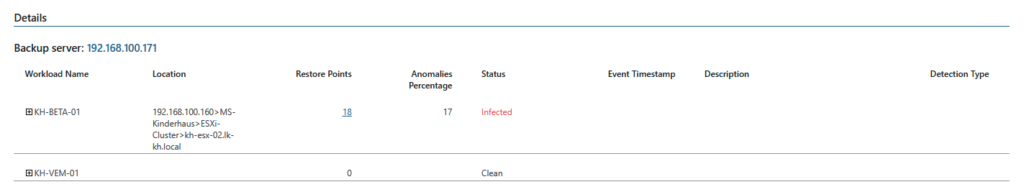
Upon clicking on the number of Restore Points (as shown in the lower screenshot), information regarding the time of the infection is now displayed based on the infected Restore Points:

As a recommended action, Veeam ONE suggests the isolation of the affected system:
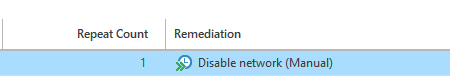
If this action is executed (‘Resolve’), the network adapter of the affected VM will be deleted, thus achieving network isolation for the concerned system. The process took less than a minute and was entirely managed through Veeam ONE:
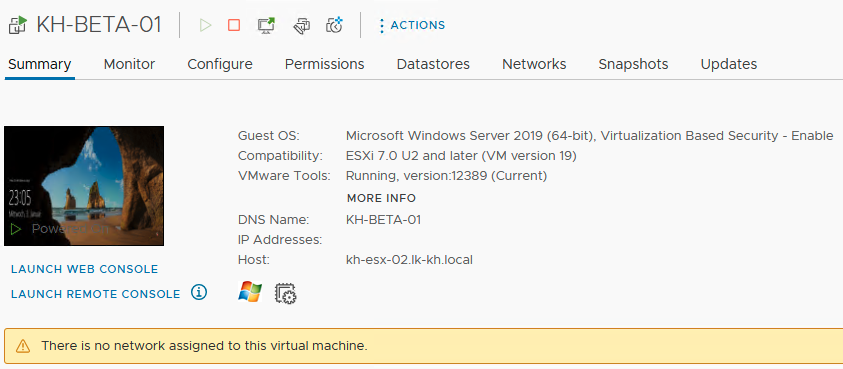
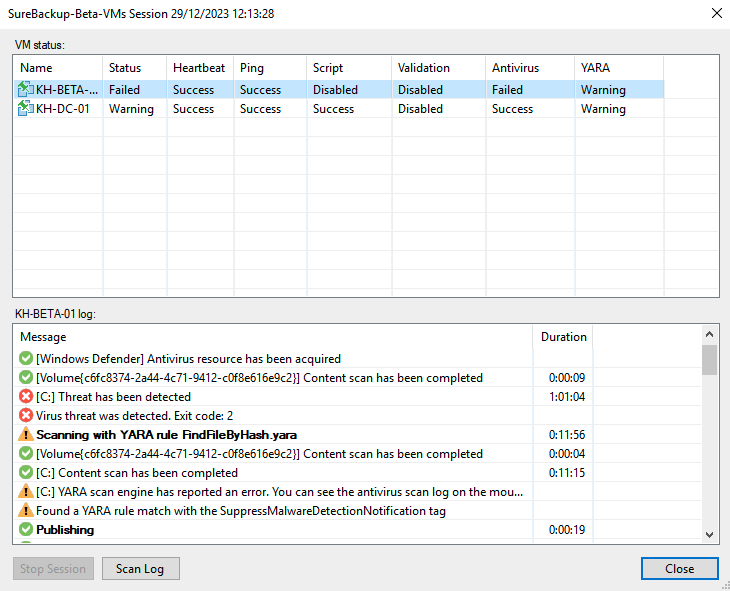
Malware detection and antivirus scan in SureBackup:
The aforementioned functionality is also available for Veeam SureBackup. Within the lab, I have defined the following settings for a SureBackup job:
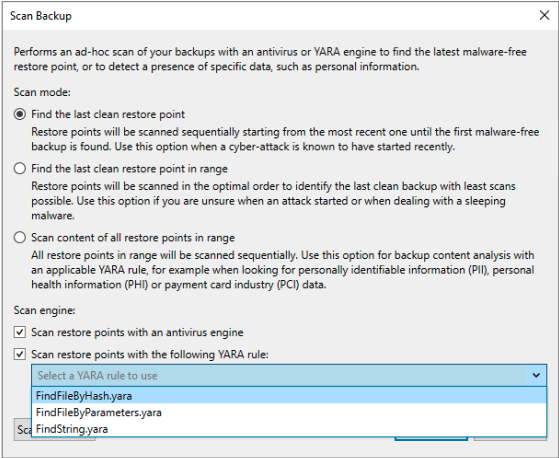
During its execution, the job performs the following steps:

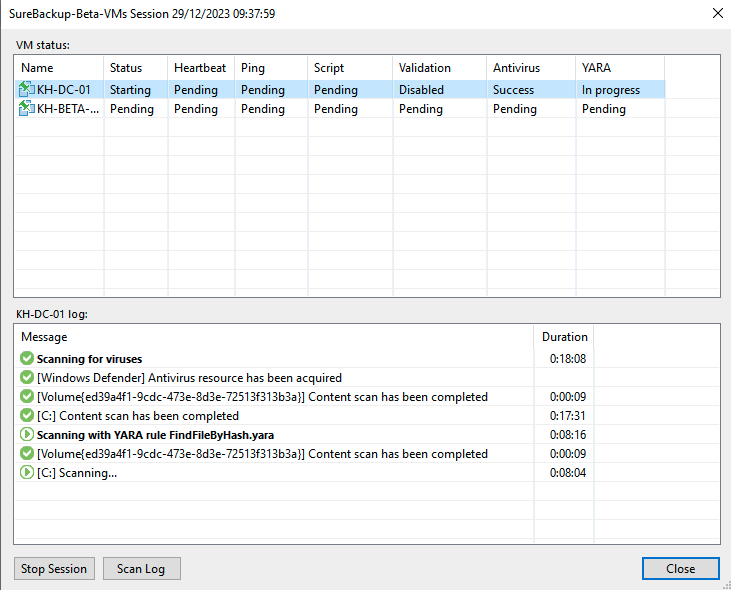
Conclusion:
Veeam’s new version represents a milestone in threat analysis and data protection. It is generally assumed that in the event of a cyberattack on the production system, backups are also compromised, as attackers often reside in the system for many months before becoming active and initiating post-exploitation.
With the new features of Veeam v12.1, there is an increased chance to detect potential malware or similar threats in backups before the outbreak of malicious software or the initiation of attacks. This not only improves the system’s recoverability but also allows for proactive measures in the production system before an attack is fully executed.
Official information about the new Veeam version can be found here:
