This year is all about community!
For the first time, I had the opportunity to deliver my own presentation on a self-chosen topic at the Veeam User Group (VUG) Germany. The second VUG Germany meeting this year was hosted in Munich by Pure Storage GmbH, who kindly provided us with catering and their facilities.
It was quite a journey for me—over three days (two of which were travel days), I drove approximately 16.75 hours, taking along a colleague from the Frankfurt area whom I met at VeeamON 2024 in Miami. That’s the spirit of community!
Networking has always been and continues to be essential to me. Equally important is delivering a message: The world keeps turning. And with it, the technological landscape of IT evolves—especially in my focus area, Disaster & Recovery.
In my view, it’s long overdue to move away from “black-and-white” thinking and avoid focusing on a single specialization without acknowledging its intersections with other fields. This mindset shaped my presentation topic:
Veeam Hardened Design – Beyond the basics
We live in an era of digital threats and highly complex, automated technologies that demand a different kind of care and foresight compared to five or ten years ago. The transformations driven by COVID-19 have significantly contributed to this shift.
It’s crucial to understand that backup strategies—both organizational and technical—must evolve, integrating multiple disciplines. In my example, these are Backup and IT Security.
The fastest, most reliable backup is worthless if it is unencrypted and conveniently stored in the same Layer-2 domain as the production workloads. We gain no value by sticking to default configurations and taking the easy route, as attackers are well aware of these standards, making them significant security risks.



Objective of my presentation:
Veeam has been offering a very useful tool within the Veeam Backup & Replication console for several versions now—yet it is far too underutilized: the Veeam Security & Compliance Analyzer.
This tool provides crucial first insights into the state of our environment, addressing not just technical but also organizational aspects. For instance, it checks for the presence of a 3-2-1 architecture, air-gapping, and much more.
But for me, that’s not enough…
I firmly believe that the underlying Windows operating system, in its “default” state (post-installation without adjustments), inherently poses a significant security risk. This is inevitable, as Microsoft can only establish a single standard, which customers then need to customize according to their specific requirements and planned applications.
Unfortunately, due to time constraints, lack of expertise, or convenience, this customization is often neglected. Applications will still run flawlessly on default-configured systems, but in the realm of security, “defaults” often come with considerable risks.
The vision:
My goal is to harden the Windows stack beneath Veeam Backup & Replication as much as possible—without relying on additional third-party software—and to go much deeper than the aforementioned script achieves.
The challenge:
Customers are often overwhelmed by the sheer volume of small adjustments required, quickly losing track. Furthermore, the added value of these efforts is frequently underappreciated, with the focus typically placed on rapid deployment and ease of use.
The adjustments I have planned are time-intensive, which presents an additional barrier for many customers.
The solution:
PowerShell! I aim to develop a standardized script that automates Windows hardening, ideally in an interactive manner with prompts and user input. This script should be executed before installing Veeam Backup & Replication, ensuring a clean and secure baseline for subsequent software deployment.
Due to the complexity and numerous factors involved, the development and testing of this script will require considerable time. My cautious goal is to complete and release a first version by the end of 2024 (mid to late December).
The final script will be made available on the Veeam Community Hub for everyone. I eagerly welcome constructive feedback and suggestions for improvement.
The presentation:
I designed the presentation to be engaging for both end customers (from a consulting perspective) and technical partners. Below are some slides I presented in Munich (unfortunately only available in German):

As mentioned earlier, I am not a big fan of additional tools, software, or similar add-ons on Disaster & Recovery components. In critical situations, the system must operate reliably and according to predefined standards and procedures. Therefore, it is important to me to minimize potential sources of errors.
An exception to this could be an MFA tool, such as Cisco Duo (see below).



Note: These tools have been available since Veeam v12.2.
For more information, please refer to additional community posts:
https://community.veeam.com/blogs-and-podcasts-57/veeam-12-2-rbac-enhancement-8494
Veeam Decoys:
https://community.veeam.com/blogs-and-podcasts-57/veeam-decoys-project-8241





The topic of Active Directory is, of course, not solely a Disaster & Recovery matter but should be viewed from a global perspective. I have highlighted excerpts of the recommended measures here. However, the Veeam Community offers a wealth of excellent content on this topic:
https://community.veeam.com/groups/cyber-security-space-95


Monitoring / Auditing:
This topic is unfortunately often overlooked in the context of Disaster & Recovery.
As we all know, it is impossible to achieve 100% security, and attack vectors will always exist—they cannot be entirely eliminated.
This makes it even more important to ensure transparency. Transparency is critical for both production and Disaster & Recovery environments, as we want to receive at least warnings when deviations from the defined standard occur. Examples of this are mentioned in the presentation.
Potential tools for this purpose could include ServiceNow or PRTG, among others.
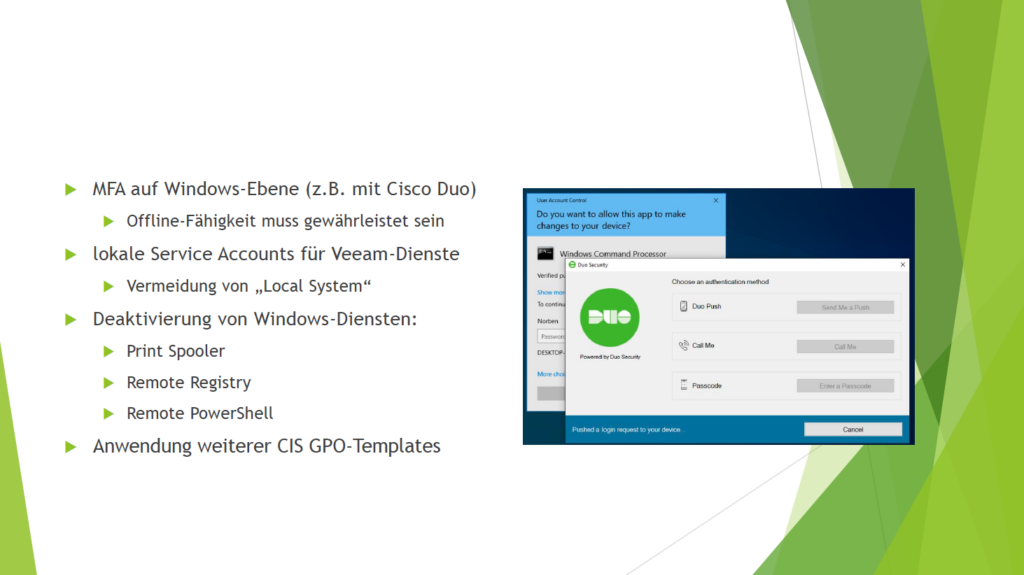
MFA with Cisco Duo:
This is another insight gained from my past experiences. Cisco Duo is an excellent tool for implementing MFA at the Windows level—whether for RDP sessions or local logins. It adds an additional layer of protection against unwanted or unauthorized logins.
One of Cisco Duo’s key advantages is its offline functionality, making it suitable for isolated environments. Regardless of how or where the tool is deployed, a clean, consistent, and comprehensive documentation (e.g., an emergency manual) is essential!
For instance, Cisco Duo can also secure administrative command-line access (CMD/Command Prompt). This means that even within an active session, the tool can be selectively deployed if the security concept allows for it.
Looking ahead:
I plan to conduct additional technical tests with Cisco Duo in the Veeam context and share the results with the community.
Stay tuned!
